Digital Forensics and Cybercrime Investigation: Techniques and Challenges
Batuhan Dilek
Tampere University
Tampere / Finland
batuhan.dilek@tuni.fi
batuhandlek@gmail.com
Abstract
This paper investigates the techniques and challenges of digital forensics and cybercrime investigations. All harmful behavior which is directly or indirectly related to computer are called cybercrime [1]. Nowadays, most of the crime involves computer systems. Therefore, the demand for cybercrime investigations is going up. All crimes are a subject to an investigation. Cybercrimes are no exception. Incorporating results from research papers, webpages and open-source resources, this paper shows the meaning of cybercrime and it’s categories, moreover, it mentions about the techniques and challenges for the digital forensics and cybercrime investigations.
Keywords-cybercrime, crime, cyber investigation, investigation, digital forensics, static analysis, live analysis
INTRODUCTION
Cybercrime has become one of the most significant threats to society. It has started to be mentioned like real life crimes all over the news. Moreover, with the advancment of computer systems and technologies and the integration of mobile phones and computer systems with society, most of the crimes can be concidered as a cybercrime. The reason is that, all harmful behaviour which is directly or indirectly related to computers are called cybercrime [1]. These cybercrimes can have serious impacts on several domains. The impacts can affect industries and society overall. Based on a research published by Ponemon Institute, median annualized cost of cybercrime is $$ 5.9$ million. The research is done on 50 largersized organizations in various sectors. For each organization the cost is within the range of $$ 1.5$ million and $$ 36.5$ million per year [2]. For the last five years, cyber bullying is one of the worst fears for a teenager under the age of eighteen [2]. Cyberbullying and other cybercrimes that targets humanbeings can lead to severe mental and physical health problems and even suicide [3].
Since most of the crimes like fraud, drug trafficking, terrorism, child exploitation and homicide usually involves computers nowadays, investigations are starting to heavily rely on digital evidence [4].
II. CYBERCRIME
A. What is cybercrime?
Wide range of criminal activities that are carried out using digital devices and computer networks are called cybercrime [5]. Activities like, identity theft, fraud, data breaches, computer viruses, scams, exploiting vulnerabilities in order to get unauthorized access in a system, stealing information, service disrupting, cyberbullying, cyberdefemation and many other that harms individuals and organizations are counted as cybercrime. These examples can be categorized under four titles: Data crime, Network Crime, Access Crime and Related Crime [2].
B. Categories of Cybercrime
1) Data Crime
Intercepting, modifying and stealing of any kind of flowing data can be listed under this category. One of the most well-known attack, the Man-In-The-Middle cyberattack can be given an example for this category.
2) Network Crime
Disrupting any network by inputting, deleting, surpressing, deteriorating, damaging or altering network data can be counted as a network crime. Denial of Service attacks, Spoofing, ARP-Poisoning, Sniffing attacks are common attack vectors that are being used against networks.
3) Access Crime
Any attempts on gaining unauthorized access on a system or malicious software that is hidden in another software like Macros, Trojans, Spywears can be considered as an access crime. An attacker may try BruteForcing into a system or SQL-Injection vector can be utilized in order to get past the authorization of the system.
4) Related Crime
This category stresses more on real-life related crimes. Aiding and abetting cybercrimes like hosting a website which allows drug or arms trafficking, or contentrelated cybercrimes like doxing, SWATing, cyberbullying, child-exploitation, cyberdefamation can be considered as related crimes.
III. INVESTIGATING CYBERCRIME AND DIGITAL FORENSICS
Crime investigation can be complicated and frustrating. Every crime has its own infrastructres, connections, people, gangs etc. Investigations can involve multiple fields like psychology, medicine, chemistry and the list can go on. Cybercrime is not not that different from real-life crimes. Internet is a vast collection of interconnected networks and each network contains its own infrastructres, technologies and resources. The enormous amount of access devices, services, various criminal behaviour and the tons of exploitable technology at hand, each situation is unique to itself [6]. Due to this fact, it becomes challenging to fit cybercriminal investigations into a standard task list approach that most of the law enforcments follow to investigate crimes. However, whenever the logical steps of cybercrime and investigative mindset are combined together, a logical model with key stages of cybercrime for investigation can be derived [7].
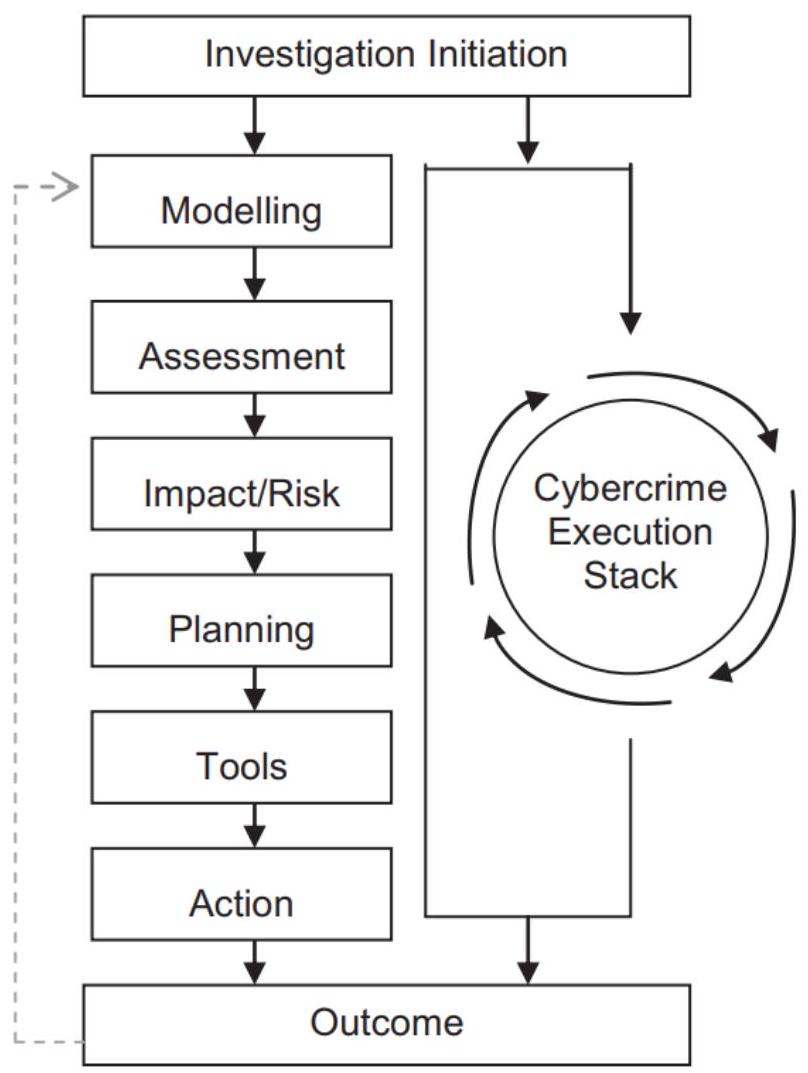
Figure 1 Stages of Cybercrime Investigations [7]
IV. TECHNOLOGIES
There are technologies and tools that makes analysis and extracts information from machines and computers alike to support the investigations. There are two types of analysis. Static and Live analysis.
A. Static Analysis
Static analysis focuses on information from disk copies to extract files, deleted files, memory contents, web browsing history, connections, login history etc. [8]. This analysis gives an understanding of what kind of activites are being conducted within the computer. The data is being acquired from external devices like hard drives, USBs and CDs. For the data that is stored internally, memory dumping technique is used. To dump memory, tools like FTK Imager can be used.
However, static analysis has many shortcomings. There are multiple limiting factors that affects the ultimate result. Shutdown process, encrypted data, incomplete evidence, single snapshots can criticaly affect the final result. Shutting down the system includes many more shutting down processes. Closing all applications, terminating all services can alter, modify or delete data or files that may be crucial for the investigation. There may be scripts that can vipe vital data from the memory whenever it senses an investigation on the computer [9]. Encrypted data can be another challenge for the static analysis. If the investigated computer is usinng encrypted volumes or files, after shutdown, to access to memory, investigator needs a key to access to storage media, which is stored in the memory and not available after shutdown. Investigators may use snapshots to investigate the machine. Still, the snapshot must be selected very carefully to get the important data. If the selected snapshot is poorly selected, vital data may be lost.
Therefore, using static analysis can provide incomplete evidence. While it gives the complete image of the system before shutdown, it lacks to provide the systems dynamic state [10].
B. Live Analysis
The difference of the live analysis from the static analysis that, static analysis is conducted on devices that are turned off or not functional. In live analysis, information is gathered while the system is still functional. Live analysis can give better and clearer results than static analysis [8]. There are many approaches, using standard interface, imported utilites, modified system and additional hardware [11]
Investigators can use standard user interfaces, imported utilities, modified systems and additional hardware to investigate a crime on a functioning system. Standard user interfaces can be used to interact with the whole system.
Investigators can use UIs for monitoring and investigating the operating system. Command shells, secure shells and telent connections can be used. This method of approach is the simplest way to interact with the system. There is no need for additional hardware or software to extract and monitor the data. By simply interacting with the system, investigator can acquire, users, processes, open ports, scheduled tasks, and many more. However, using user interfaces has their own limitations and challenges. For example, an investigator may need proper level of access into a system. Which will lead to another process called privilege escalation. Using user interfaces poses a danger to system integrity as well. Usage of rootkits and other techniques may violate system integrity and most of the evidence can be altered or deleted.
Some hardware makes it possible to copy memory from a running sysyem into another external memory such as Hard drives and USBs. The overall point for additional hardware is to attach the external hardware to one of the system busses and initiating direct memory access. From direct memory access, the external hardware should transact the data from the compormised machine to an external memory. This method of approach most of the time needs a preinsallation. After the installation, the compormised operating system may react in a bad way. Some kernel level scripts may override and alter vital information about the system based on the detected hardware behaviour.
Overall, even if there are shortcomings of the mehtods of live analysis, it’s results are much more reliable in comparison to static analysis since, live analysis is conducted on dynamic and functional systems.
C. Tools for Digital Forensics and Analaysis
In this section, some tools that are being used in realworld scenarios to conduct digital forensics and analaysis are mentioned. There are numerous amount of tools that are ready to serve depending on the situation. As it is mentioned in the paper, each cybercrime is unique to itself and it may need various tools to conduct an investigation on the compormised system. Depending on the requirements, investigator should chose the correct combinations of tools. Here, we understand the importance of the stages of cyber investigation. One needs to decide on what kind of data that is expected to be extracted, what kind of a system is the compromised system, what kind of access control there is on the system, what are the protective measures are activated and other requirements. Thus modelling the the overall approach and doing a risk assesment first, and then planning, selecting tools and taking action makes investigation goes smoothly as possible.
Below table depicts the popular tools in digital forensics, their main operating system and their mode of analysis.
| Tool | OS | Static/Live |
|---|---|---|
| FTK | Windows | Static |
| Wireshark | Windows/Linux/Mac | Both |
| SIFT | Ubuntu | Live |
| The Sleuth Kit | Windows/Linux | Live |
| EnCase | Windows | Static |
| CAINE | Linux | Both |
| WFT (Windows Forensic Toolkit) | Windows | Live |
REFERENCES
[1] Wall, D. S. (2001). Cybercrimes and the Internet. Crime and the Internet, 1-17.
[2] Das, S., & Nayak, T. (2013). Impact of cybercrime: Issues and challenges. International journal of engineering sciences & Emerging technologies, 6(2), 142-153.
[3] John, A., Glendenning, A. C., Marchant, A., Montgomery, P., Stewart, A., Wood, S., … & Hawton, K. (2018). Self-harm, suicidal behaviours, and cyberbullying in children and young people: Systematic review. Journal of medical internet research, 20(4), e9044.
[4] Casey, E. (2009). Handbook of digital forensics and investigation. Academic Press.
[5] Wikipedia contributors. (2024, March 31). Cybercrime. Wikipedia. https://en.wikipedia.org/wiki/Cybercrime
[6] Stelfox, P. (2013). Criminal investigation: An introduction to principles and practice. Willan.
[7] Hunton, P. (2011). The stages of cybercrime investigations: Bridging the gap between technology examination and law enforcement investigation. Computer Law & Security Review, 27(1), 61-67.
[8] Rafique, M., & Khan, M. N. A. (2013). Exploring static and live digital forensics: Methods, practices and tools. International Journal of Scientific & Engineering Research, 4(10).
[9] Hay, B., Bishop, M., & Nance, K. (2009). Live analysis: Progress and challenges. IEEE Security & Privacy, 7(2), 30.
[10] Hay, B., Bishop, M., & Nance, K. (2009). Live analysis: Progress and challenges. IEEE Security & Privacy, 7(2), 31.
[11] Hay, B., Bishop, M., & Nance, K. (2009). Live analysis: Progress and challenges. IEEE Security & Privacy, 7(2), 31 - 32.